Work from Home
Configure your office computer for telework in less than a minute. Securely access your office computer from home or from a mobile device. Screen sharing technology enables you to efficiently work remotely at any time, from anywhere in the world.
Sign Up Download ISL Light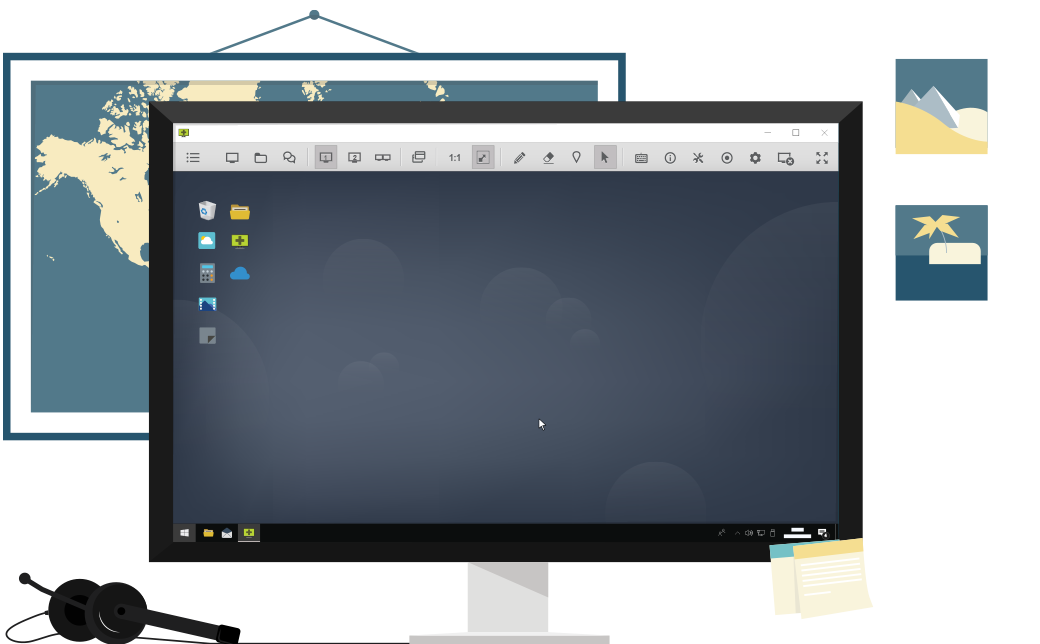
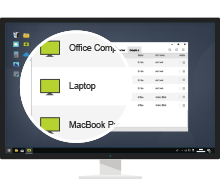
Access Unattended Computer
Control Remote Desktop
View the screen and control a remote computer.
Connect via RDP
You don’t have to set up the VPN to be able to use your RDP access. ISL Online allows you to easily route Microsoft Remote Desktop Protocol or Secure Shell (SSH) sessions through a secure tunnel, and connect to unattended computers running in the remote network without using a VPN or making any firewall changes. The best thing is, you can set this up in minutes.
Video Tutorialslink
Watch video tutorials that guide you through using ISL Online software.
Enable Multiple Users to Work from Home
Set up remote access to a large number of computers within your organization and get your colleagues ready to telework. Conceptually, there are 3 milestones you will need to reach.
- Milestone 1: Create a list of users (teleworkers) within your organization.
- Milestone 2: Deploy remote access agent (ISL AlwaysOn) to office computers.
- Milestone 3: Pair office computers and teleworkers to define which employee has remote access to which office computer.
A simple manual below will guide you through the process and help you reach the milestones.
Manual | Setup Telework
Milestone 1
1. Create ISL Online Account
Please follow the sign up link to create an ISL Online account.
Sign up nowOnce you register your ISL Online account, you will need to choose your preferred hosting option:
- a) Cloud (recommended - set by default)
- b) Self-Hosted (for big companies) Read manual
- c) Managed private cloud (for big companies with very specific requirements)
2. Register a Domain
Upon signing up, a randomly named domain will be created. Rename it to your company name or whatever suits you the best, for example "mycompany1".
3. Create a Main User
Create a main user account (for example \\mycompany1\mainuser) which will be used to manage lists of teleworkers and office computers.
4. Create a Computer Group
Create a computer group (for example "remotework"). The group should be owned by the main user.
5. Define Teleworkers
a) Organization with a few employees
If you need to arrange remote access to office computers for only a few employees within your organization, you should manually create user accounts for them.
b) Organization with a large number of employees
If you need to arrange remote access to office computers for a large number of employees within your organization, you should create a CSV (Comma Separated Values) file that lists the necessary user information (users.csv).
"Full name" , "Email" , "Username"
"John Doe" , "john.doe@mycompany1.com" , "john_doe"
"Jane Doe" , "jane.doe@mycompany1.com" , "jane_doe"
Once you have a list of users ready, visit https://www.islonline.com/account/hosted-service/users.htm and click "Import Users from CSV". After importing, direct your users to https://www.islonline.com/login/password-forgot.htm where they can set their password.
Milestone 2
6. Set Unattended Access
To enable remote access to office computers within your organization, you will need to install a remote access agent called ISL AlwaysOn on those computers.
a) Organization with a few employees
If you need to install ISL AlwaysOn on a small number of computers within your organization, you should simply walk from one computer to another and run the installer on each computer.
During the installation process you will manually configure each computer to be shared with the appropriate target user(s). By doing so, the process of setting up remote access will be successfully completed for you.
Please only continue reading this manual if you need to set up remote access for a large number of users and computers within your organization.
b) Organization with a large number of employees
If you need to deploy a remote access agent to a large number of office computers within your organization, please contact us via email (support@islonline.com) or visit our live chat.
Our team will prepare a customized link for an ISL AlwaysOn executable which includes the grant blob and sample password (it will set both the global access password and the connection password), with instructions on how to replace the password.
You can use the provided customized link for a mass deployment of the remote access agent to office computers by utilizing your IT asset management system or similar solutions.
You should test the provided customized link on a few machines before you massively deploy it to all computers.
You should create a CSV (Comma Separated Values) file that lists the necessary computer information (computers.csv) for all office computers which you would like to make securely accessible remotely.
"Computer name" , "Target username"
"WORKGROUP\JOHNDOEPC" , "john_doe"
"WORKGROUP\JANEDOELAPTOP" , "jane_doe"
Once you have a list of users ready, please contact us via email (support@islonline.com) or visit our live chat and we will import your list of computers into the system within your main user account.
Milestone 3
On our side, we will also execute a special script which will pair a list of users with a list of computers. Technically, this means that each computer will only be shared with the appropriate target user(s).
The last step of the bulk on-boarding process is to perform a "forgot password" procedure for all users.
Each user should follow the password reset link received via email, set a new password and log in to the system to see the appropriate computer(s) in their list.
Initial (bulk) on-boarding procedure complete!
7. Future Onboarding
a) Organization with a few employees
For each additional user you should manually create an additional user as described in 5.a and configure remote access for such user as described in 6.a.
b) Organization with a large number of employees
If there are a lot of additional users and/or computer sharing adjustments needed, another set of input files needs to be prepared (users2.csv and/or computers2.csv), and we will run the appropriate scripts again.
Offer the Highest Securitylink

Symmetrical AES 256 Bit Encryption

Your own certificates for encryption

ISO/IEC 27001:2022 certified

Two-factor authentication

GDPR compliance

Security and penetration tests

External authentication
(LDAP, SAML 2.0. etc.)

Automatic session recording
Learn more about ISL Online security
Try 15 Days For Free
Enjoy your new remote desktop experience!
All features included. No credit card required.